In recent years, this torturous, technological crime has been receiving wide media coverage. The media have reported the effects of what is now called the “Havana Syndrome,” since the first cases originated in Havana, Cuba.
When the name “Havana Syndrome” was first reported, over 2,000 diplomats and security agency staff, mainly from the USA and Canada, stated that strange and very distressing symptoms were happening in and on their bodies. These symptoms were not new. They had already been occurring for decades, in over 21 other countries, under different names: V2K (Voice to Skull) technology and DEW (Directed Energy Weapons) technology.
These technologies are a global targeting program, centred around human experimentation of the brain, control over a person, and the advancement of A. I. (Artificial Intelligence).
Below is a brief outline of the aspects involved as part of the development of cyber torture of victims.
Organised Stalking or – “Gang Stalking”

Organised stalking, commonly known as “Gang Stalking,” is carried out by enthusiastic, structured groups. Some are civilians who are approached, and are paid, to carry out the development of these technologies and to monitor their victims daily.
During and after WW2 the German Police, named “The Stasi,” were surveiling civilians during much public unrest. Initially, the tactics used were severe. Eventually, “no-touch torture” was introduced, intended to intimidate, and psychologically weaken the target. It was called “Zersetzung”. It has been investigated and found that the Stasi used X-ray devices in a directed and weaponised manner to cause long-term health problems in its opponents.
In 1956 in the U.S.A., the FBI began “COINTELPRO”—short for Counterintelligence Program. The U.S. Government claimed this was set up to infiltrate and stop groups, such as the Ku Klux Klan. They publicly ceased Cointelpro in the 70’s but secretly continued and today it is still operational.
Victims are followed, intimidated, sabotaged, and isolated. It is often the case that victims will experience the same people monitoring them. Breaking and entering the victim’s home is common and is highly reported. This is done to plant covert monitoring devices and to follow every move of the victim.
Victims often hire private detectives, once they realise, they are being monitored. They then find that their stalkers are hired by, or working for the Government, agencies, and police. The stalkers have clearances and access to all the victim’s emails and accounts.
Through V2K technology, where subliminal messages and thoughts are transmitted into a victim, “Street Theatre” can take place. The victim is fed information that certain people are involved in their monitoring and that they are being followed everywhere.
Electronic Harassment

Another aspect is hacking and cyber stalking. Any passwords, accounts including social media accounts, emails and even banking accounts can easily be monitored and sabotaged. Some report that loans are taken out in their names, illegally.
It is well known that victims end up having to be vigilant and back up important files in ways which they should not have to do.
Due to their high-level clearances, and advanced hacking and monitoring capabilities, the criminals involved can usually achieve their goals without being traced. We also know that various Intelligence agencies around the world monitor people Illegally. The N.S.A. monitor people all over the world and keep records of all communications.
Part of the evidence the victim has is that hacking can be detected and proven. By using IP addresses and network monitoring Apps and software, an individual can see if others are using the victim’s personal networks & IP addresses.
Electronic Attacks – Nervous system manipulation

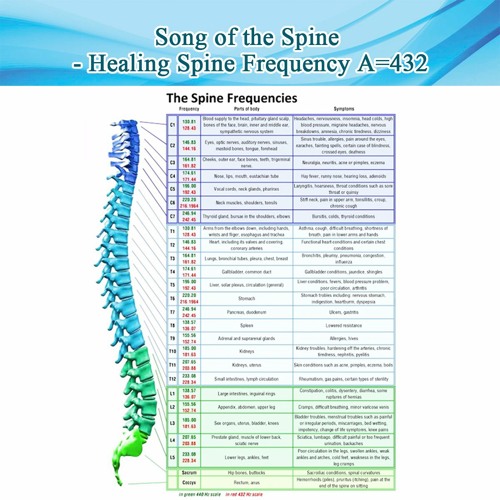
Using highly advanced Microwave Weapons Systems, which can come in many different forms, victims can be attacked via manipulation of the Central Nervous System. Signals are sent to the Spinal cord using Tone Generators. Each vertebrae have a different tone – these are referred to as “Song of the Spine”.
Signals are sent, which are then translated by the brain and the victim experiences actual physical pain, as a result. The attacks are real and damaging on the skin and other internal areas of the body.
There are only few types of RF or microwave signals which can operate in such a way to penetrate multiple obstacles, such as buildings and walls. These signals also work when a person is underwater and on a plane. The fact the attacks do not stop whilst travelling on a plane, and once the victim is in a foreign country, proves that satellites are being used.
When a person moves to a remote location, attackers can often use drones which provide recalibration to different satellites. There are satellites in orbit just for the purpose of remote areas. The fact that satellites are being used tells us that telecommunication companies either know about these transmissions or are involved. In many cases, satellites used for the public do not reach areas that military satellites can.
Devices such as mobile phones, tablets, laptops and more can be accessed and hacked into, via signals, for them to transmit back from satellite or 5G towers, directly into the victim. This is an easy method used to attack victims.
Companies making such devices and weapons are DARPA / Lockheed Martin / Boeing / NASA and many more. DARPA have their own Brain Initiative program. There is also now the AG Barr Pre-Crime program.
The transmissions are very specific and have pinpoint precision. DEW (Directed Energy Weapons), transmit massive electrical shocks and waves /pulses or energy which leave severe radiation burns on the victims’ skin. DEW and lasers are all being used by militaries around the world.
Victims will usually find they have high toxic chemicals and metals in their systems because of the severe radiation exposure. Symptoms can lead to serious health conditions such as Auto Immune disorders and cancer.
BCI & RNM – Brain Computor Interface & Remote Neural Monitoring

The innocent victim has also provided research and medical technologies which are used in a positive way. Examples are Parkinson’s Disease and Dementia. This is known as DBS – Deep Brain Stimulation. A patient will CONSENT to an Implant in their brain and a BCI for doctors to aid in their treatment.
These technologies are being used by Elon Musk and companies such as NEXTMIND. Headsets have been developed which allow a person to control their devices, via their thoughts, i.e., without having to touch the devices.
For the victims of V2K technology and DEW, NON-CONSENSUAL implants and/or chips cause serious neurological damage such as seizures, cognition issues, emotional, visual, memory loss, basic body movements, nausea, dizziness, balance, and speech issues. It allows the criminal access to, and control over, every part of the victim’s brain. This is known as Remote Neural Monitoring. Essentially, this provides attackers control over the life of a person.
Voice to Skull – V2K – Subliminal Messaging – “The Frey Effect”

Most victims complain of symptoms commonly referred to as “Voices”. When experiencing this for the first time it can be extremely distressing. Doctors pass the victim off as schizophrenic, however schizophrenia happens to people in their 20’s and not in their 30’s, 40’s, 50’s and beyond. The voices are in real time and the criminals can comment or transmit thoughts, via computer transmission, within nano seconds.
The criminals use what are known as “Vox Changers”, into the cochlea, to disguise voices and to make the experience more disturbing. The disguise is computer-generated most of the time They can, for example, emulate the voice of a family member of the victim and transmit images of that family member into the victim’s brain. This may make the victim believe that even his/her loved ones may be involved in the crime.
.
Implants or RFID Chips, Hydrogel Sensors, Nano-Tech

The attacks can be achieved simply by the victim receiving EMF transmissions. Usually, victims have been implanted with some form of chip or chips, within their bodies. Implanted. Non-con-sensually and Illegally.
When victims become aware of their attacks, they think back to any surgical procedure they have had. In many cases, doctors, surgeons, and scientists have been paid ‘under the table’ to implant victims. National Health care services can be paid to involve themselves in these so-called ‘research programs. The implanting may have also been performed just after the victim’s birth.
Over the years, these chips or Implants have become more and more advanced. Hydrogel sensors have been used for medical research. They can be injected, rubbed onto the skin or even put into a drink.
Hydrogels thrive in water and expand in the bloodstream. Nano Technology is also often referred as “Smart Dust”. It is used in food packaging, the growing of crops, medical gauzes and more. Once in the system, they can never be removed.
Some chips can be easily moved around the victim’s body in order that attacks can be made to different areas.
Some can be injected, or actual surgery is required. Some victims report break ins to their home and marks appearing on their bodies the next day.
Some consumers are nowadays choosing to have RFID chips implanted into various body parts. There are many companies around the world offering this technology. These consumers have chips implanted into their hands so that they can, for example, make payments, open doors, start their cars because the RFID chip’s signal provides this option instead of the person using a card or a key.
Dr Staninger is a toxicologist who has written a book about implants –
Conclusion
History has shown that because patients are not aware of what unscrupulous doctors, scientists and surgeons will do, to make extra money/monies, they become victims of illegal research and greed. This is murder and a war crime. Many victims have been murdered because of inhumane treatment and torture, be it the result of brain or nerve damage or radiation exposure, via V2K technology and/or microwave waves (EMF). Victims have submitted to diseases, cancer and in many cases have committed suicide.
Please see our “Documents” page to view various patents for these patents and technologies.
